- John The Ripper 0 Password Hashes 1 Left Hand Grips
- John The Ripper 0 Password Hashes 1 Left Hand Piano
- John The Ripper 0 Password Hashes 1 Left Hand Retrieve Speed Spool Combo
Option) might be already cracked by previous invocations of John. (The message printed in that case has been changed to 'No password hashes left to crack (see FAQ)' starting with version 1.7.7.) To display cracked passwords, use 'john -show' on your password hash file(s). To force John to crack those same hashes again, remove the john.pot file. Now if you want to see the cracked passwords give john the following arguments:./john./zip.hashes -show. It should output something like:./test.zip:test4321. 1 password hash cracked, 0 left. Note: the hash file should have the same type of hashes. For example, we cannot put the rar AND zip hashes in the same file.

Practice ntds.dit File Part 6: Password Cracking With John the Ripper – Wordlist
John The Ripper 0 Password Hashes 1 Left Hand Grips
After password cracking examples with hashcat, I want to show you how to crack passwords with John the Ripper (remember we also produced hashes for John the Ripper: lm.john.out and nt.john.out).
First we use the rockyou wordlist to crack the LM hashes:
Option –wordlist specifies the wordlist to use, and option –pot specifies the pot file I want to create/use.
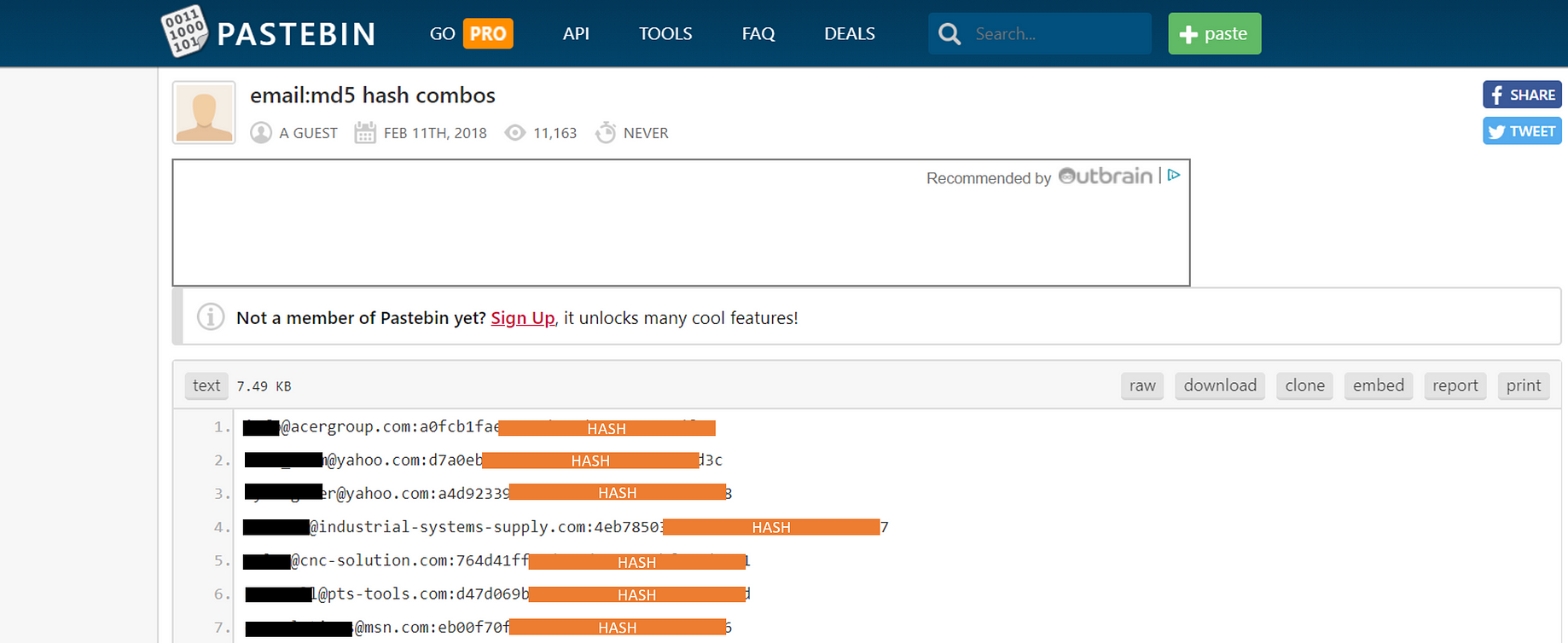
Output:
John The Ripper 0 Password Hashes 1 Left Hand Piano
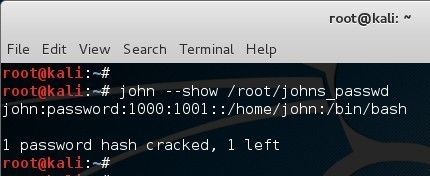
And then we use option –show to display the (partially) recovered passwords:
Output:
Cracking NTLM hashes is done with a similar command, it’s just the name of the files that changes:
Output:
And then we use option –show to display the recovered passwords:
John The Ripper 0 Password Hashes 1 Left Hand Retrieve Speed Spool Combo
Output: